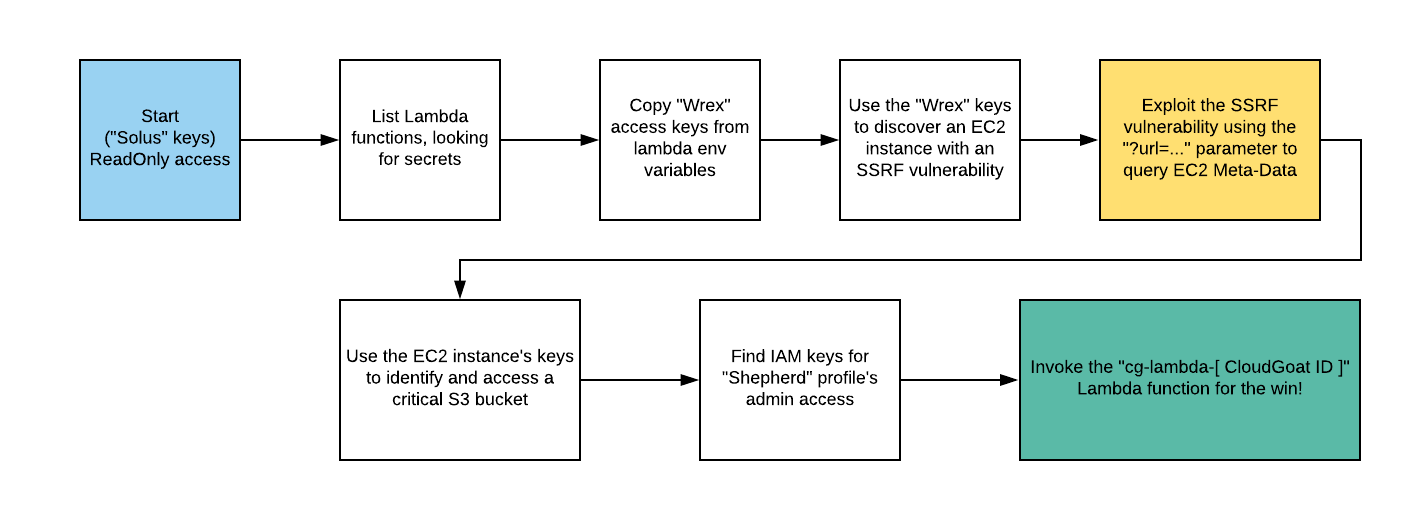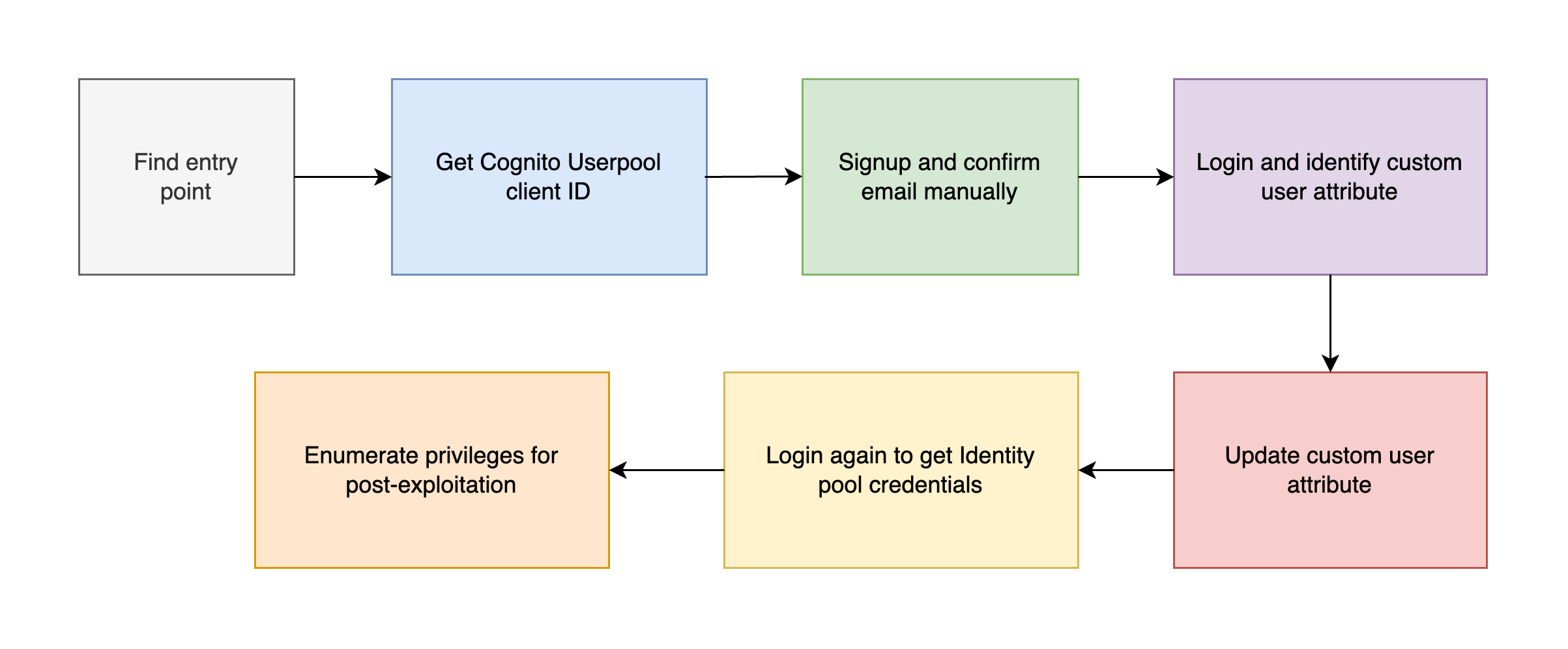
AWS Privilege Escalation via Vulnerable Cognito ~ CloudGoat
In this post, I’ll cover how the vulnerable Cognito service can be exploited to escalate privileges and obtain temporary AWS credentials. Privilege Escalation via Vulnerable Cognito Introduction AWS Cognito is commonly used to handle user authentication and identity federation in cloud applications. However, when misconfigured, it becomes a gateway for privilege escalation, especially when: Frontend validations are trusted too much Custom attributes are used to control access Identity Pools are mapped to roles based on unvalidated claims This scenario demonstrates how misconfigured Amazon Cognito setups can be exploited to gain unauthorized access to AWS resources. You’ll simulate an attacker exploiting weak client-side validations and improperly scoped custom attributes to escalate privileges and extract AWS credentials via Cognito Identity Pools. ...