2000$ bounty, How I Chained Recon and IDOR to Access 100's of Credit Cards
The author explains how combining reconnaissance and an IDOR vulnerability led to unauthorized access to hundreds of credit card records. Medium.

The author explains how combining reconnaissance and an IDOR vulnerability led to unauthorized access to hundreds of credit card records. Medium.
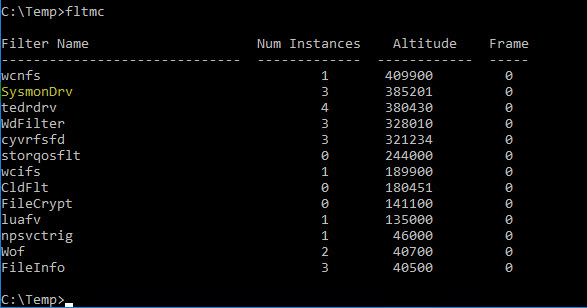
In this post, I’ll walk you through a stealthy evasion technique that involves modifying the Sysmon driver’s altitude. how altitudes affect kernel monitoring, and how attackers can abuse this mechanism to disable or crash security tools, without ever touching the EDR itself. ...
Read the full post on Hacklido.
Read the full post on Hacklido.