
TL;DR Why you shouldn't doubt yourself while giving OSCP
Preparing for the OSCP can be overwhelming, I totally get it. There are moments where self-doubt creeps in, especially when things don’t go as planned in exam. In this post, I’ll share some tips that helped me push through and pass the exam. Why You Shouldn’t Doubt Yourself While Giving OSCP The OSCP exam is as much a mental battle as it is a technical one. If you’ve ever doubted yourself during this journey, I’ve been there too and this post is for you. I’ll walk you through how I went from completely underprepared to finally cracking the exam after a focused sprint. Maybe this will help you see that it’s never too late to shift gears and get it done. ...
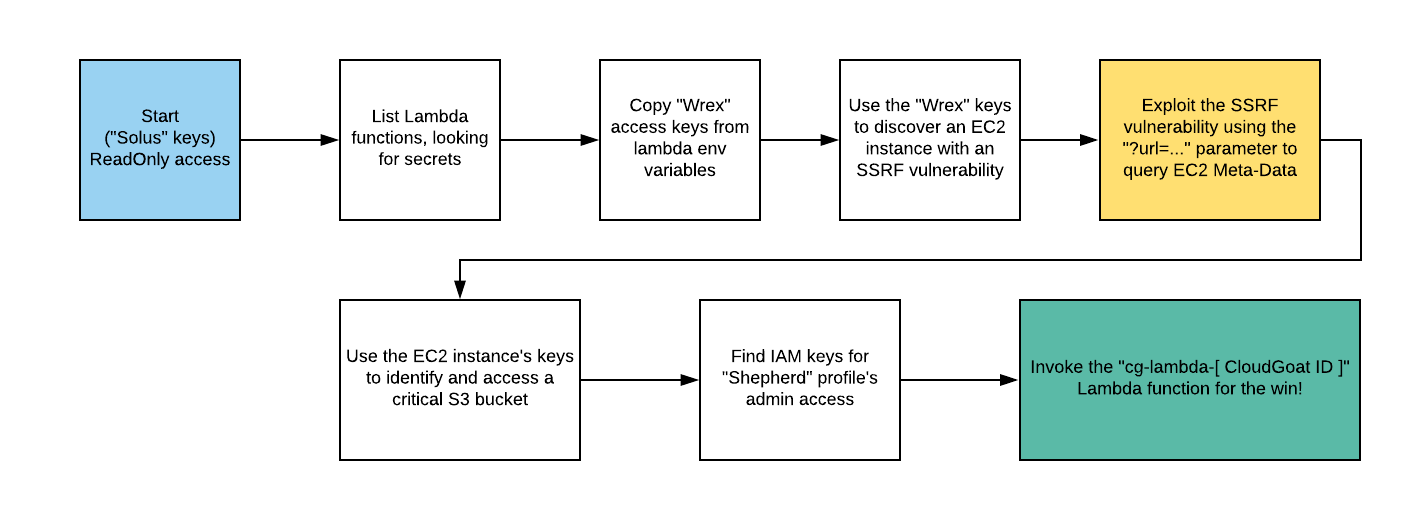

](/images/socks5.png)