Build, Break, Repeat — I’m a passionate security researcher :)
Currently, I’m working on ⚔️ detection, containment, and understanding adversarial behaviors to harden systems before the next move is made.
Currently, I’m working on ⚔️ detection, containment, and understanding adversarial behaviors to harden systems before the next move is made.

In this post, I’ll walk you through a stealthy evasion technique that involves modifying the Sysmon driver’s altitude. how altitudes affect kernel monitoring, and how attackers can abuse this mechanism to disable or crash security tools, without ever touching the EDR itself. ...

In this post, I’ll walk you through a stealthy evasion technique that involves modifying the Sysmon driver’s altitude. how altitudes affect kernel monitoring, and how attackers can abuse this mechanism to disable or crash security tools, without ever touching the EDR itself. ...

In this post, I’ll walk you through a a critical vulnerability in React Server Components (RSC). Tracked as CVE-2025-55182 and widely known as React2Shell, the flaw enables unauthenticated remote code execution (RCE) in applications using the React Server Components Flight protocol. ...
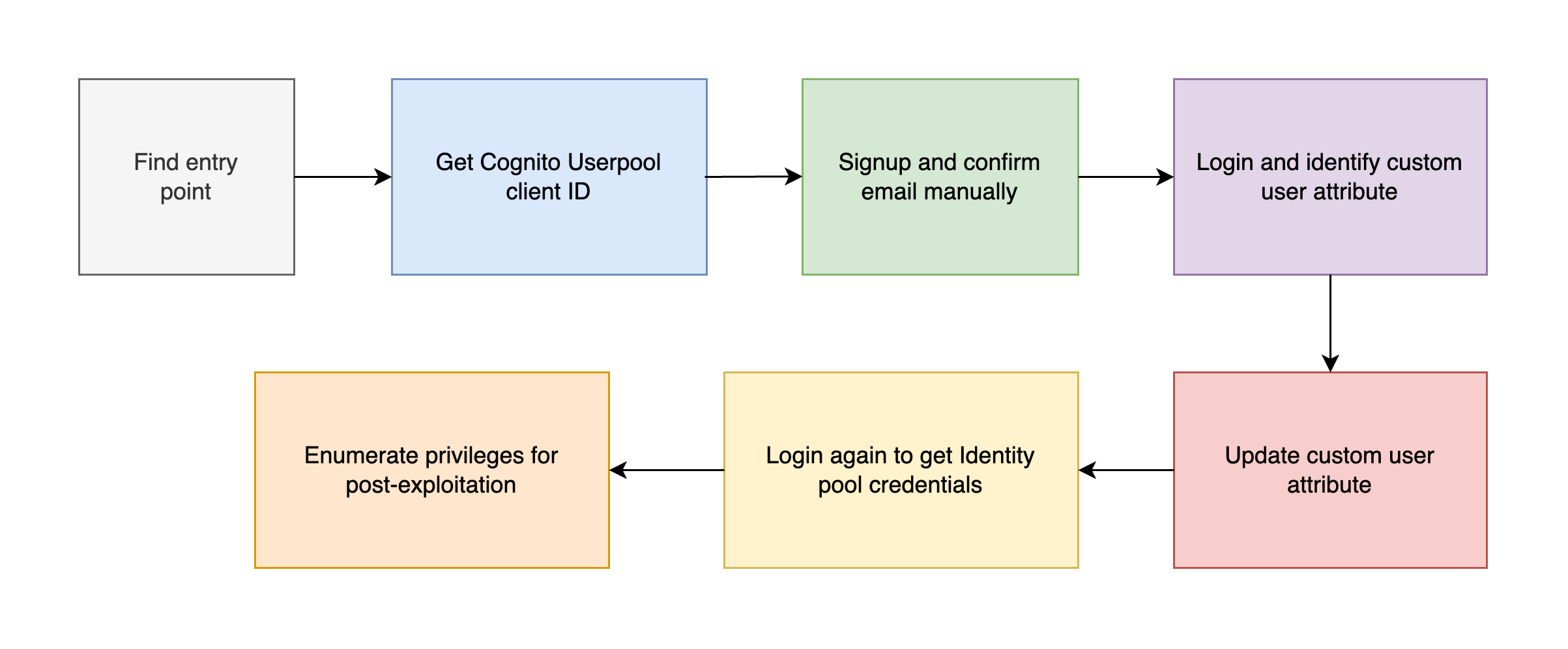
In this post, I’ll cover how the vulnerable Cognito service can be exploited to escalate privileges and obtain temporary AWS credentials. Privilege Escalation via Vulnerable Cognito Introduction AWS Cognito is commonly used to handle user authentication and identity federation in cloud applications. However, when misconfigured, it becomes a gateway for privilege escalation, especially when: Frontend validations are trusted too much Custom attributes are used to control access Identity Pools are mapped to roles based on unvalidated claims This scenario demonstrates how misconfigured Amazon Cognito setups can be exploited to gain unauthorized access to AWS resources. You’ll simulate an attacker exploiting weak client-side validations and improperly scoped custom attributes to escalate privileges and extract AWS credentials via Cognito Identity Pools. ...